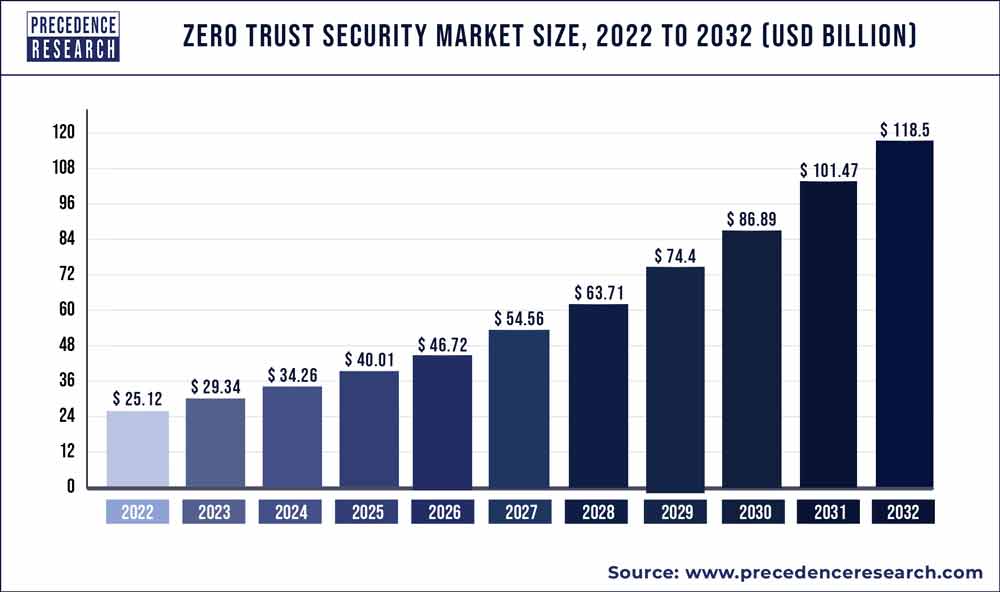
The global zero trust security market size was estimated to be around US$ 25.12 billion in 2022. It is projected to reach US$ 25.12 billion by 2032, indicating a CAGR of 16.78% from 2023 to 2032.
The market research report on the Zero trust security market provides a comprehensive analysis of various key aspects. It includes the definition, classification, and application of Zero trust security products. The report examines the development trends, competitive landscape, and industrial chain structure within the industry. Furthermore, it presents an overview of the industry, analyzes national policies and planning, and offers insights into the latest market dynamics and opportunities at a global level.
Get a Sample: https://www.precedenceresearch.com/sample/3170
Zero Trust Security Market Report Scope
| Report Coverage | Details |
| Market Size in 2023 | USD 29.34 Billion |
| Market Size by 2032 | USD 118.5 Billion |
| Growth Rate from 2023 to 2032 | CAGR of 16.78% |
| Largest Market | North America |
| Base Year | 2022 |
| Forecast Period | 2023 To 2032 |
| Segments Covered | By Authentication Types, By Solution Type, and By Deployment Type |
| Regions Covered | North America, Europe, Asia-Pacific, Latin America, and Middle East & Africa |
Read More: Cardiovascular Digital Solutions Market Size to Garner USD 183.23 Billion by 2032
The report presents the volume and value-based market size for the base year 2022 and forecasts the market’s growth between 2023 and 2032. It estimates market numbers based on product form and application, providing size and forecast for each application segment in both global and regional markets.
Focusing on the global Zero trust security market, the report highlights its status, future forecasts, growth opportunities, key market players, and key market regions such as the United States, Europe, and China. The study aims to present the development of the Zero trust security market by considering factors like Year-on-Year (Y-o-Y) growth, in addition to Compound Annual Growth Rate (CAGR). This approach enables a better understanding of market certainty and the identification of lucrative opportunities.
Regarding production, the report investigates the capacity, production, value, ex-factory price, growth rate, and market share of major manufacturers, regions, and product types. On the consumption side, the report focuses on the regional consumption of Zero trust security products across different countries and applications.
Buyers of the report gain access to verified market figures, including global market size in terms of revenue and volume. The report provides reliable estimations and calculations for global revenue and volume by product type from 2023 to 2032. It also includes accurate figures for production capacity and production by region during the same period.
The research includes product parameters, production processes, cost structures, and data classified by region, technology, and application. Furthermore, it conducts SWOT analysis and investment feasibility studies for new projects.
This in-depth research report offers valuable insights into the Zero trust security market. It employs an objective and fair approach to analyze industry trends, supporting customer competition analysis, development planning, and investment decision-making. The project received support and assistance from technicians and marketing personnel across various links in the industry chain.
The competitive landscape section of the report provides detailed information on Zero trust security market competitors. It includes company overviews, financials, revenue generation, market potential, research and development investments, new market initiatives, global presence, production sites, production capacities, strengths and weaknesses, product launches, product range, and application dominance. However, the data points provided only focus on the companies’ activities related to the Zero trust security market.
Prominent players in the market are expected to face tough competition from new entrants. Key players are targeting acquisitions of startup companies to maintain their dominance. The report
Reasons to Purchase this Report:
- Comprehensive market segmentation analysis incorporating qualitative and quantitative research, considering the impact of economic and policy factors.
- In-depth regional and country-level analysis, examining the demand and supply dynamics that influence market growth.
- Market size in USD million and volume in million units provided for each segment and sub-segment.
- Detailed competitive landscape, including market share of major players, recent projects, and strategies implemented over the past five years.
- Comprehensive company profiles encompassing product offerings, key financial information, recent developments, SWOT analysis, and employed strategies by major market players.
Key Players
- Cisco Systems, Inc.
- Palo Alto Networks, Inc.
- Microsoft Corporation
- Symantec Corporation (now part of Broadcom Inc.)
- Okta, Inc.
- IBM Corporation
- Check Point Software Technologies Ltd.
- Akamai Technologies, Inc.
- Fortinet, Inc.
- CyberArk Software Ltd.
Zero Trust Security Market Segmentations
By Authentication Types
- Single-factor Authentication
- Multi-factor Authentication
By Solution Type
- Network Security
- Data Security
- Endpoint Security
- API Security
- Cloud Security
- Others
By Deployment Type
- Cloud
- On-Premises
By Geography
- North America
- Europe
- Asia-Pacific
- Latin America
- Middle East and Africa
TABLE OF CONTENT
Chapter 1. Introduction
1.1. Research Objective
1.2. Scope of the Study
1.3. Definition
Chapter 2. Research Methodology (Premium Insights)
2.1. Research Approach
2.2. Data Sources
2.3. Assumptions & Limitations
Chapter 3. Executive Summary
3.1. Market Snapshot
Chapter 4. Market Variables and Scope
4.1. Introduction
4.2. Market Classification and Scope
4.3. Industry Value Chain Analysis
4.3.1. Raw Material Procurement Analysis
4.3.2. Sales and Distribution Channel Analysis
4.3.3. Downstream Buyer Analysis
Chapter 5. COVID 19 Impact on Zero Trust Security Market
5.1. COVID-19 Landscape: Zero Trust Security Industry Impact
5.2. COVID 19 – Impact Assessment for the Industry
5.3. COVID 19 Impact: Global Major Government Policy
5.4. Market Trends and Opportunities in the COVID-19 Landscape
Chapter 6. Market Dynamics Analysis and Trends
6.1. Market Dynamics
6.1.1. Market Drivers
6.1.2. Market Restraints
6.1.3. Market Opportunities
6.2. Porter’s Five Forces Analysis
6.2.1. Bargaining power of suppliers
6.2.2. Bargaining power of buyers
6.2.3. Threat of substitute
6.2.4. Threat of new entrants
6.2.5. Degree of competition
Chapter 7. Competitive Landscape
7.1.1. Company Market Share/Positioning Analysis
7.1.2. Key Strategies Adopted by Players
7.1.3. Vendor Landscape
7.1.3.1. List of Suppliers
7.1.3.2. List of Buyers
Chapter 8. Global Zero Trust Security Market, By Authentication Types
8.1. Zero Trust Security Market, by Authentication Types, 2023-2032
8.1.1 Single-factor Authentication
8.1.1.1. Market Revenue and Forecast (2020-2032)
8.1.2. Multi-factor Authentication
8.1.2.1. Market Revenue and Forecast (2020-2032)
Chapter 9. Global Zero Trust Security Market, By Solution Type
9.1. Zero Trust Security Market, by Solution Type, 2023-2032
9.1.1. Network Security
9.1.1.1. Market Revenue and Forecast (2020-2032)
9.1.2. Data Security
9.1.2.1. Market Revenue and Forecast (2020-2032)
9.1.3. Endpoint Security
9.1.3.1. Market Revenue and Forecast (2020-2032)
9.1.4. API Security
9.1.4.1. Market Revenue and Forecast (2020-2032)
9.1.5. Cloud Security
9.1.5.1. Market Revenue and Forecast (2020-2032)
9.1.6. Others
9.1.6.1. Market Revenue and Forecast (2020-2032)
Chapter 10. Global Zero Trust Security Market, By Deployment Type
10.1. Zero Trust Security Market, by Deployment Type, 2023-2032
10.1.1. Cloud
10.1.1.1. Market Revenue and Forecast (2020-2032)
10.1.2. On-Premises
10.1.2.1. Market Revenue and Forecast (2020-2032)
Chapter 11. Global Zero Trust Security Market, Regional Estimates and Trend Forecast
11.1. North America
11.1.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.1.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.1.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.1.4. U.S.
11.1.4.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.1.4.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.1.4.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.1.5. Rest of North America
11.1.5.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.1.5.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.1.5.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.2. Europe
11.2.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.2.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.2.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.2.4. UK
11.2.4.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.2.4.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.2.4.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.2.5. Germany
11.2.5.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.2.5.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.2.5.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.2.6. France
11.2.6.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.2.6.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.2.6.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.2.7. Rest of Europe
11.2.7.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.2.7.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.2.7.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.3. APAC
11.3.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.3.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.3.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.3.4. India
11.3.4.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.3.4.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.3.4.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.3.5. China
11.3.5.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.3.5.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.3.5.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.3.6. Japan
11.3.6.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.3.6.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.3.6.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.3.7. Rest of APAC
11.3.7.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.3.7.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.3.7.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.4. MEA
11.4.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.4.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.4.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.4.4. GCC
11.4.4.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.4.4.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.4.4.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.4.5. North Africa
11.4.5.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.4.5.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.4.5.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.4.6. South Africa
11.4.6.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.4.6.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.4.6.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.4.7. Rest of MEA
11.4.7.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.4.7.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.4.7.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.5. Latin America
11.5.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.5.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.5.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.5.4. Brazil
11.5.4.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.5.4.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.5.4.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.5.5. Rest of LATAM
11.5.5.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.5.5.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.5.5.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
Chapter 12. Company Profiles
12.1. Cisco Systems, Inc.
12.1.1. Company Overview
12.1.2. Product Offerings
12.1.3. Financial Performance
12.1.4. Recent Initiatives
12.2. Palo Alto Networks, Inc.
12.2.1. Company Overview
12.2.2. Product Offerings
12.2.3. Financial Performance
12.2.4. Recent Initiatives
12.3. Microsoft Corporation
12.3.1. Company Overview
12.3.2. Product Offerings
12.3.3. Financial Performance
12.3.4. Recent Initiatives
12.4. Symantec Corporation (now part of Broadcom Inc.)
12.4.1. Company Overview
12.4.2. Product Offerings
12.4.3. Financial Performance
12.4.4. Recent Initiatives
12.5. Okta, Inc.
12.5.1. Company Overview
12.5.2. Product Offerings
12.5.3. Financial Performance
12.5.4. Recent Initiatives
12.6. IBM Corporation
12.6.1. Company Overview
12.6.2. Product Offerings
12.6.3. Financial Performance
12.6.4. Recent Initiatives
12.7. Check Point Software Technologies Ltd.
12.7.1. Company Overview
12.7.2. Product Offerings
12.7.3. Financial Performance
12.7.4. Recent Initiatives
12.8. Akamai Technologies, Inc.
12.8.1. Company Overview
12.8.2. Product Offerings
12.8.3. Financial Performance
12.8.4. Recent Initiatives
12.9. Fortinet, Inc.
12.9.1. Company Overview
12.9.2. Product Offerings
12.9.3. Financial Performance
12.9.4. Recent Initiatives
12.10. CyberArk Software Ltd.
12.10.1. Company Overview
12.10.2. Product Offerings
12.10.3. Financial Performance
12.10.4. Recent Initiatives
Chapter 13. Research Methodology
13.1. Primary Research
13.2. Secondary Research
13.3. Assumptions
Chapter 14. Appendix
14.1. About Us
14.2. Glossary of Terms
Contact Us:
Mr. Alex
Sales Manager
Call: +1 9197 992 333
Email: sales@precedenceresearch.com
